Behavioural Analytics
an organised crime be prevented by predicting people’s characteristics, networks, and intentions from the way they have previously behaved? This new programme takes advantage of technological advancements and data from ‘social signals’ to assess the threat of actors and make inferences about their likely actions. This programme is led by Paul Taylor, Stacey Conchie and David Ellis at Lancaster University.
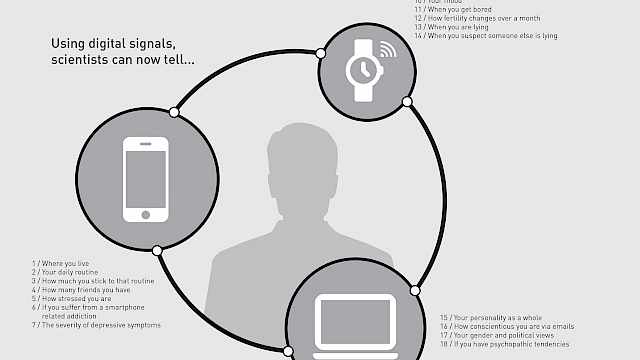
Work in this programme is focused on understanding what can be inferred about groups from streams of behavioural data. Our efforts are unashamedly theory driven and much of the programme’s focus is on deriving more efficient measures through a solid understanding of what aspects of behaviour matter (i.e., correspond) to the inference in question. This approach seeks to dramatically decrease the complexity of the data model rather than find more efficient ways to handle the complexity. Our work includes examining digital traces of behaviour that are produced through a person’s use of technology and the internet.
Research Focus
Specifically, the early focus of this programme conducts original research exploring:
- How criminal group activity to be understood in real time.
- How behavioural markers can reveal characteristics about organised crime groups.
- How a group’s behaviour can predict how successful they’ll be in fulfilling their criminal intent.
- How language markers in digital communication can predict the effectiveness of criminal groups.
Research Findings
So far, this programme has generated insights such as:
- Providing groups with mis-information when undergoing a group task reduces their language co-ordination.
- The age and gender of a person can be predicted from their smartphone behaviours such as screen time and application use.
A synthesis of papers which use language style matching to understand conversation patterns has also been created and published here: https://psyarxiv.com/yz4br/
Topics of future investigation
Future directions of the programme aim to assess behavioural analytics in order to:
- Understand the relative value of social sensor data for remote assessment.
- Explore ‘atypical’ or ‘suspicious’ patterns of behaviour that may indicate an imminent attack.
- Assess behaviour longitudinally and identify behavioural anomalies which may be a precursor of criminal behaviour.
Project resources
Academic Publications
Same Kind of Different: Affordances, Terrorism, and the Internet
The rapid development of the Internet as a cornerstone of private and social life has provoked a growing effort by law enforcement and security agencies to understand what role the Internet plays in terrorism. Paul Gill, Emily Corner, Maura Conway, Amy Thornton, Mia Bloom, and John Horgan's (2017, this issue) effort to identify empirically when and how terrorists engage with the Internet is thus timely and important.
Understanding when terrorists use the Internet is valuable for investigators who must evaluate the immediacy of the risk posed by a suspect or cell. Knowing the typical patterns of use (or lack of use) can facilitate inferences about a cell's preparedness, the nature of its support, and even the goal of its attack. Understanding how terrorists use the Internet is essential for policy makers who must construct legislation to deter citizens from terrorism while retaining their rights to freedom.
This is arguably best accomplished by legislation targeted at a narrow set of Internet uses that are, as far as possible, exclusively associated with illegal actions.
In this policy essay, we focus on two of Gill et al.’s (2017) main contributions. We argue that, subject to robust independent replication, they encourage thought about the functions of the Internet for terrorists, which in turn may have implications that offer useful guidance for policy and practice. Alongside the article's conceptual contributions, Gill et al. also assert to have resolved several pragmatic challenges and we suggest ways in which their solutions, if developed fully, could offer value to the security analyst community. Finally, we take stock of where Gill et al.’s contribution has left us and review the next steps.
(From the journal abstract)
Taylor, Paul J., Donald Holbrook, and Adam Joinson. 2017. ‘Same Kind of Different’. Criminology & Public Policy 16 (1): 127–33. https://doi.org/10.1111/1745-9133.12285.