Article
David Buil-Gil, Jose Pina-Sánchez, Ian Brunton-Smith, Alexandru Cernat
Bad Data, Worse Predictions
Article
Sophie Nightingale
Identity fraud in the digital age
Article
Marion Oswald
‘Give Me a Ping, Vasili. One Ping Only’ Why the Success of Machine Learning Depends on Empowered People
Article
Isabelle van der Vegt, Bennett Kleinberg, Paul Gill
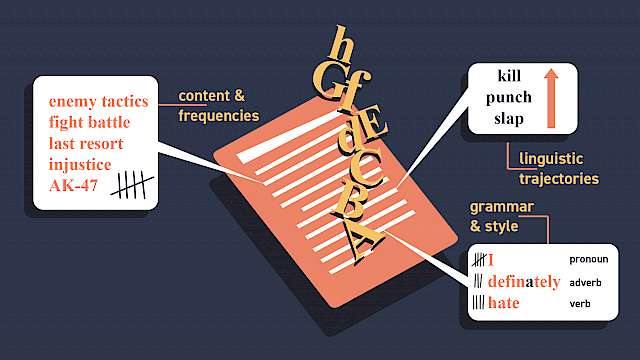
Linguistic Threat Assessment: Challenges and Opportunities
Article
Oli Buckley, Heather Shaw, Leon Reicherts, Richard Philpot, Mark Levine
Technology Lightning Articles
Article
Mapping a new biometrics landscape
Article
Carl Miller
China’s Digital Diplomacy
Article
Chris Baber
Why AI Systems Need to Explain Themselves
Article
Erin Grace, Gina Ligon
NCITE: The designated counter terrorism and targeted violence research centre for the US Department of Homeland Security
Article
Zoe Marchment, Paul Gill
Evaluating the Channel Programme’s Vulnerability Assessment Framework
Article
Shanon Shah
How (Not) To Make A Violent Copycat: Lessons From ‘Dark Fandoms’