We often refer to criminal and extremist groups as ‘networks’ and it is increasingly common to try to map, measure, and analyse these networks using the techniques of formal social network analysis.
Early academic work on such networks tended to assume that the desire to avoid detection and apprehension would lead to the network being structured in particular ways and, according to some, to a trade-off between the demands of secrecy or security on one side and those of efficiency on the other.
However, empirical studies point to variation in network structure in practice, reflecting different strategies of maintaining secrecy as well as the very different conditions in which covert networks take shape, the many different contingencies which their members must negotiate and the difficulties of shaping a real-world network according to a preconceived plan.
In light of this, it makes sense to reflect upon some of the ways in which network structures can vary and the different strengths and vulnerabilities of these structures. In doing this we should recognise that we are discussing ideal types, only approximated in practice, and that properties of social networks do not automatically or necessarily have the effects to which I refer, given the intelligent, inventive, and adaptive nature of their human nodes, and the complex nature of human social relations.
Here I discuss two axes of variation: centralisation-decentralisation and density-sparsity (see Figure 1).
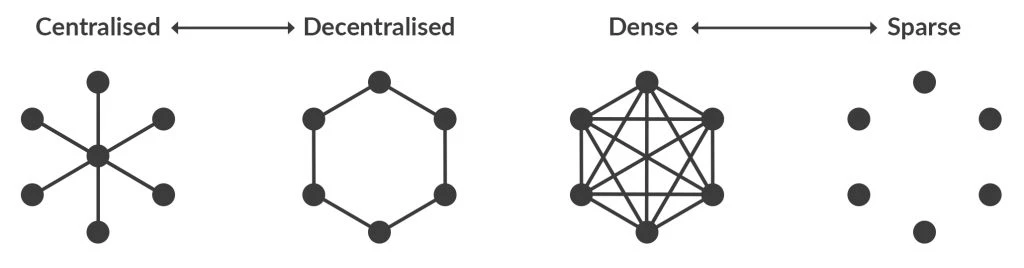
Figure 1: Variations in Network Structure
In the simple case, a social network is highly centralised when a large proportion of the people in it (‘nodes’ in network science-speak) are directly connected to a small number of ‘hub nodes’. Centralisation makes the network less vulnerable to the damaging effect of a loss of nodes, even a relatively high proportion of nodes in a big network if such losses are random. This is because hubs hold the network together when even a sizeable proportion of nodes are removed, and yet hubs comprise only a tiny proportion of all nodes in the network, so they are very unlikely to be affected by random factors removing or disabling nodes.
In addition, centralisation can contribute to resilience in covert networks – at least if hubs hold authority – because they can maintain a close eye on other network members, imposing and enforcing security protocols across the whole network, which will protect it.
However, centralised hubs tend to be visible in a network and this makes them vulnerable. Communication always leads back to them and most other nodes in the network are in a position to compromise them. Hubs will likely be the focus of disabling efforts but the removal of a hub (through arrest, for instance) may not disable a criminal network, as others will take their place, learn from their mistakes and the network will bounce back determined to avenge their loss.
Rivals and police and security forces will deliberately seek out central figures in a network
Decentralisation within a network enables important figures (however they may be defined) to remain more concealed and less vulnerable when others are compromised. However, it also makes efforts to direct activity within the network more difficult. The movement of resources is typically slower; information can become distorted when passed through many hands; and coordination is more difficult to achieve.
Furthermore, an increase in the number of exchanges required to move resources or information around a network itself increases the risk of detection. Every exchange runs the risk of inviting attention or interception.
Network density refers to the number of connections in a network, considered as a proportion of all possible connections. High density is often taken to be conducive to the generation of higher levels of trust, cooperation and mutual support in networks, if only because it increases mutual surveillance between network members and enforcement of norms by way of sanctions. This can increase the resilience of the network by reducing the risk of defection and enforcing security protocols.
Where people do defect, however, this will be more damaging as they have information about and contact with a higher proportion of others in the network.
Recruiting a single person as an informant will afford the police and security services access to a significant proportion of the network because that person will be connected to a high proportion of others. Militant and criminal networks are often dense when they draw upon strong pre-existing connections, such as those of family, neighbourhood or church.
Research on the UK suffragettes suggests that their network became sparser as their militancy increased
Mindful of the risk which ties to others may pose to their own security, individuals involved in illegal activity may seek to minimise their connections to and dependence upon others, leading to the generation of sparse networks. This may increase security for individual nodes, as only a small number of others in the network are able to compromise them, but at a potential cost to efficiency. Resources will take longer to flow through the network and with a greater risk that they will be damaged or compromised en route. In addition, because less constrained by the network, nodes are more vulnerable to defection and security-threatening departures from the procedure. Research on the UK suffragettes suggests that their network became sparser as their militancy increased.
Cell structures, in which nodes form dense clusters, which are, in turn, only sparsely connected to one another, offer some of the advantages of both high and low density (they are dense at the local level but sparse at the global level). However, they can be difficult to engineer, except perhaps in the periphery of a network. Insider accounts suggest that attempts to implement a cell structure within the Provisional IRA during the early 1970s were often thwarted by the existence of pre-existing relationships between members of different cells, for example.
Copyright Information
As part of CREST’s commitment to open access research, this text is available under a Creative Commons BY-NC-SA 4.0 licence. Please refer to our Copyright page for full details.






